If you are running a WordPress website, one of your biggest concerns should be security. With WordPress powering over 40% of all websites, it is no surprise that hackers often see it as an attractive target. Unfortunately, many site owners don’t realize their site has been compromised until after the damage is done.
Knowing how to tell if your WordPress site is compromised, is critical, not only for protecting your data but also for preserving your online reputation, SEO rankings, and customer trust. A hacked site can lead to devastating consequences:
- SEO losses as search engines blacklist infected sites
- Data breaches that expose sensitive customer or business information
- Loss of trust from visitors, customers, and partners
- Revenue drops caused by downtime or redirected traffic
The good news? Early detection can drastically reduce the impact of a breach. By learning the key warning signs and adopting proactive monitoring, you can spot suspicious activity before it escalates. In this guide, we will learn the most common indicators of a compromised WordPress site and provide practical steps to protect your business from long-term damage. For businesses that want expert level protection and ongoing monitoring, taking the help of professional WordPress Security Services can add an extra layer of defense against evolving threats.
Common Signs Your WordPress Site is Compromised
The faster you can recognize the warning signs of a hacked WordPress site, the easier it is to limit damage. Below are the most frequent indicators of compromise, organized by category.
Sudden Changes in Traffic or Rankings
A noticeable drop in traffic or rankings often signals that search engines or users are being redirected away from your site.
- Drop in organic traffic due to hidden redirects or malware injections
- Google Safe Browsing displaying red warnings about harmful content
Regularly reviewing your analytics and Google Search Console alerts can help you catch these issues early.
Unauthorized Content or Links
Hackers frequently insert spammy content to exploit your website’s authority.
- Spam links appearing in footers, sidebars, or even within blog posts
- Strange pop-ups or advertisements redirecting visitors to unrelated or harmful sites
This not only frustrates users but can also result in penalties from search engines.
Login & User Account Issues
Compromised login credentials are a common entry point for attackers.
- Locked-out admin accounts despite using correct passwords
- Unknown or suspicious new administrator accounts created without approval
Reviewing your user list regularly helps ensure only trusted accounts have access.
Unexpected File and Database Changes
Malware often hides within WordPress files or the database.
- Unknown scripts or files in the
/wp-content/directory - Altered or missing core files such as
index.phpor.htaccess - Suspicious scheduled tasks or cron jobs running unexpectedly
Using file integrity monitoring tools makes it easier to identify these changes.
Performance and Server Problems
Compromised sites often show strain due to malicious processes.
- Slow loading times or intermittent downtime
- Frequent 500/502/503 server errors caused by overloaded servers
- Unusual activity patterns in server logs from unfamiliar IP addresses
Security & Browser Warnings
Both browsers and search engines flag unsafe websites quickly.
- “This site may be hacked” messages in search results
- Malware or phishing alerts displayed directly in browsers
Once flagged, your site can lose user trust instantly, even if the problem is minor.
Customer or User Complaints
Often, your visitors will notice issues before you do.
- Reports of unauthorized transactions on eCommerce websites
- Emails failing to send, or customers receiving spam that appears to come from your domain
Ignoring these complaints can lead to further reputation and financial damage.
Quick Comparison: Normal vs. Compromised Behavior
| Area | Normal Behavior | Compromised Behavior |
| Traffic & Rankings | Stable or gradually growing traffic | Sudden drops, blacklisting, or redirects |
| Content & Links | Only authorized posts and links | Spam links, pop-ups, or hidden redirects |
| User Accounts | Known, authorized admins only | Unknown or suspicious new admin accounts |
| Files & Database | Clean, unchanged WordPress files | Altered, missing, or unfamiliar scripts |
| Performance | Normal load times, minimal errors | Slow speeds, frequent 500-series errors |
| Security Warnings | No alerts in browsers or search engines | “Site may be hacked” or malware alerts |
| User Experience | Smooth browsing and transactions | Complaints of spam, failed emails, fraud |
Why WordPress Sites Get Hacked
- WordPress is the most widely used content management system in the world, powering more than 40% of all websites. Its scale makes it an attractive target for hackers: a single vulnerability can expose millions of sites at once. While WordPress itself is secure, weaknesses in how site owners manage their websites often create openings for attackers.
- One of the biggest issues is poor password security. Many administrators still rely on weak or reused credentials such as “admin123” or “password.” These are easy for automated bots to guess, and when the same password is reused across multiple accounts, a breach on one platform can quickly cascade into a WordPress takeover. Enforcing unique, complex passwords and enabling two-factor authentication are simple steps that dramatically improve resilience.
- Another common vulnerability comes from outdated software. Plugins and even the WordPress core require frequent updates to patch security flaws. When these updates are neglected, attackers can take advantage of publicly documented exploits. Working with Skilled WordPress Plugin Developers helps ensure your plugins are properly maintained and secure, preventing the kind of small oversights that can lead to thousands of mass infections.
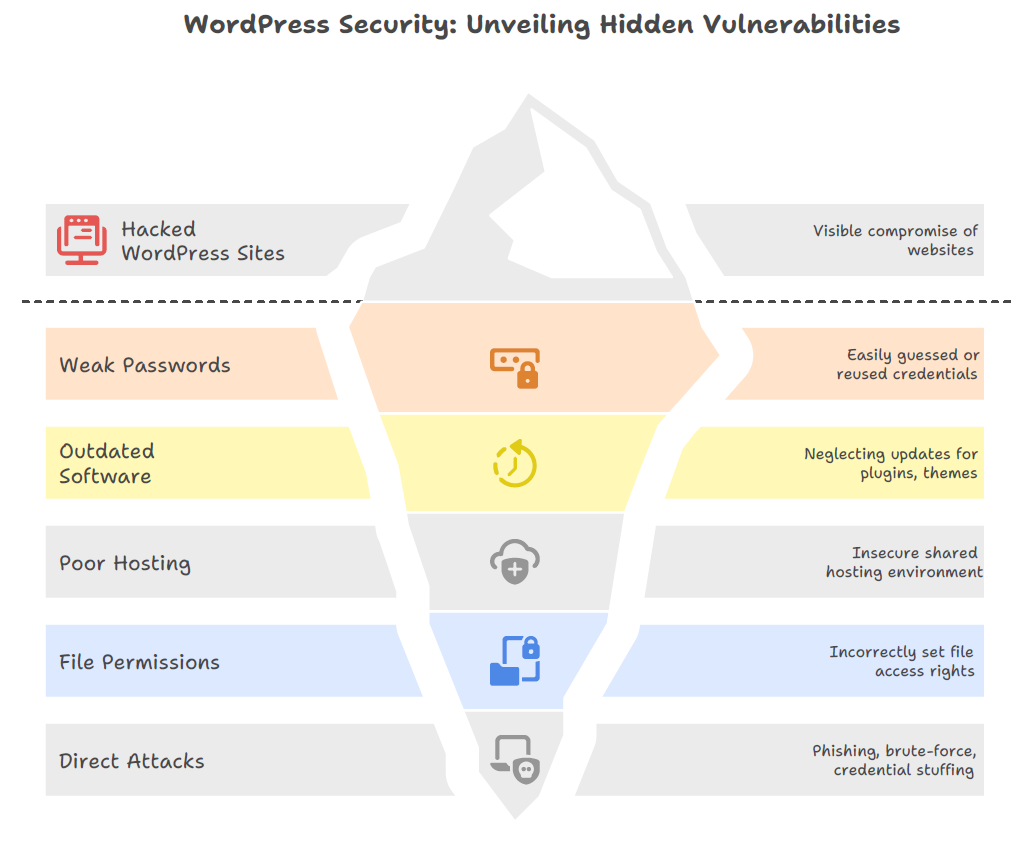
- The choice of hosting environment also plays a role. Poorly secured or shared hosting increases the risk of cross-site contamination, where one compromised site gives hackers a pathway to others on the same server. In addition, weak server configurations can allow intruders to bypass basic defenses. This is why selecting a hosting provider with strong WordPress-specific security practices is critical.
- Hackers also take advantage of insecure file permissions. File permissions determine who can read, write, or execute files on your server. If these are set incorrectly—such as overly permissive “777” settings—attackers can easily inject malicious code or escalate privileges. Following WordPress’s recommended settings helps ensure files remain protected.
- Finally, direct attack methods remain a constant threat. Phishing schemes trick administrators into handing over login credentials. Brute-force attacks use automated bots to guess passwords until they succeed. Credential stuffing takes stolen username and password combinations from unrelated breaches and tests them against WordPress login pages. Without proper safeguards like login attempt limits, CAPTCHA verification, and multi-factor authentication, these attacks can succeed in minutes.
- In short, WordPress sites aren’t inherently insecure—but mismanagement, neglect, and weak security practices make them easy targets. Understanding these entry points is the first step in building a stronger defense.
How Hackers Gain Access (Common Methods)
Understanding how attackers break into WordPress sites is the first step in defending against them. Hackers typically use a combination of technical exploits and deceptive tactics to gain control, often leaving backdoors behind to maintain access.
Backdoors and Hidden Files
One of the most common methods is the creation of backdoors—malicious files or scripts hidden within your site’s code. These backdoors allow attackers to re-enter your site even after you’ve patched the initial vulnerability. They are often disguised as legitimate WordPress files and placed in directories such as /wp-content/ or /uploads/, making them difficult to detect without a security scan.
SQL Injection and Cross-Site Scripting (XSS)
Database-driven attacks like SQL injection and XSS are also widely used.
- SQL injection occurs when attackers insert malicious queries into forms or URLs to manipulate your database. This can expose sensitive user data or give hackers administrative control.
- Cross-site scripting (XSS) injects malicious JavaScript into web pages, which then executes in visitors’ browsers. This can steal login sessions, redirect users, or spread malware.
These vulnerabilities often arise from poorly coded plugins, themes, or insecure form handling.
Malicious Redirects and Clickjacking
Hackers frequently use your site as a vehicle to drive traffic elsewhere. Malicious redirects send users to phishing, gambling, or counterfeit product sites without their consent. Clickjacking takes this a step further by tricking visitors into clicking on hidden buttons or links, often leading to compromised accounts or fraudulent transactions.
Distributed Denial of Service (DDoS) and Brute-Force Attempts
Some attacks don’t rely on hidden code but instead overwhelm your site’s resources.
- DDoS attacks flood your server with traffic until it crashes or becomes unusable. While this doesn’t always lead to a direct hack, it creates opportunities for other attacks while your defenses are strained.
- Brute-force login attempts involve automated bots guessing username and password combinations until they succeed. Without protections like rate-limiting or CAPTCHA, these attacks can eventually break through.
DNS Hijacking and Registrar-Level Compromises
Finally, not all attacks happen at the WordPress level. DNS hijacking targets the domain itself, redirecting visitors to a malicious server even if your site is secure. Similarly, if a hacker gains access to your registrar account, they can take over your domain entirely, lock you out, and control your online identity.
What to Do If Your WordPress Site is Hacked (Step-by-Step)
Discovering that your WordPress site has been hacked can feel overwhelming, but acting methodically will help you regain control and minimize long-term damage. Here’s a structured recovery process to follow.
1. Stay Calm and Put the Site in Maintenance Mode
Panic often leads to rushed decisions that can make recovery harder. Instead, place your site in maintenance mode to prevent visitors and search engines from interacting with compromised content while you investigate.
2. Check Logs and Identify Suspicious Activity
Review your server and WordPress logs for unusual login attempts, file modifications, or errors. This can help you trace the point of entry and understand how deep the compromise goes.
3. Scan for Malware and Unknown Files
Use a reputable security plugin or an external scanning tool to detect malicious scripts. Pay particular attention to unfamiliar files in directories like /wp-content/ and /uploads/.
4. Remove Backdoors and Malicious Code
Hackers often leave hidden entry points to regain access even after cleanup. Carefully delete or quarantine suspicious files, and replace altered code with fresh versions from trusted sources.
5. Restore from a Clean Backup (if Available)
If you have a recent, secure backup created before the hack, restoring it is often the fastest way to recover. Be sure to verify the backup is clean before deploying it.
6. Reset All Passwords and Remove Suspicious Users
Change every password associated with your site—admin accounts, database, FTP, and hosting. At the same time, remove any unauthorized user accounts that may have been created during the attack.
7. Reinstall WordPress Core, Plugins, and Themes
Download fresh copies of WordPress core files, your active theme, and all plugins directly from trusted repositories. Reinstalling ensures no lingering malicious code remains.
8. Clean Database and Sitemap
Check your database for injected spam content or altered tables. Similarly, review and regenerate your sitemap to remove malicious URLs that could harm your SEO visibility.
9. Resubmit to Google for Review (if Blacklisted)
If Google has flagged your site as unsafe, use Google Search Console to request a review once you’ve cleaned up. This is essential for regaining visibility in search results.
10. Test Website Functionality and User Access
Finally, ensure your website works properly for both admins and visitors. Test logins, forms, checkout processes, and email functionality to confirm that everything is back to normal.
Preventing Future WordPress Hacks
Cleaning up after a hack is only part of the process. The real priority is ensuring it doesn’t happen again. By strengthening your security practices, you significantly reduce the chances of future compromises.
Keep WordPress, Plugins, and Themes Updated
Outdated software is one of the leading causes of WordPress hacks. Hackers often exploit known vulnerabilities that have already been patched in newer versions. Make it a habit to update the WordPress core, plugins, and themes regularly, or enable automatic updates where possible.
Enforce Strong Passwords and Two-Factor Authentication
Weak or reused passwords are an easy target for brute-force attacks. Require administrators and users with elevated privileges to use strong, unique passwords. Adding two-factor authentication provides another layer of defense, even if a password is stolen.
Limit Login Attempts and Use CAPTCHAs
Automated bots will attempt thousands of login combinations until they succeed. Limiting the number of login attempts and implementing CAPTCHAs makes brute-force attacks much less effective.
Use HTTPS, Secure Hosting, and SFTP
Basic security measures also matter. Always install an SSL certificate to enable HTTPS, which encrypts data between your site and visitors. Choose a hosting provider with strong security practices, and avoid plain FTP in favor of SFTP, which securely transfers files.
Install a Reliable Security Plugin or Firewall
Security plugins such as Wordfence, Sucuri, or iThemes Security act as a first line of defense. They can block malicious traffic, detect malware, and even prevent brute-force login attempts. A firewall adds an extra layer of protection by filtering harmful requests before they reach your server.
Regularly Monitor Logs and Activity Reports
Keeping an eye on server logs and admin activity helps you spot unusual patterns like multiple failed login attempts or new user accounts, before they turn into full-scale attacks.
Set Up Automated, Off-Site Backups
Even with strong defenses, no system is completely immune. Automated backups stored off-site ensure that if your site is compromised, you can restore it quickly without losing critical data.
FAQs on WordPress Security
How often do WordPress sites get hacked?
WordPress is the most popular CMS, which naturally makes it a target. According to security reports, thousands of WordPress sites are hacked every day, often through outdated plugins, weak passwords, or vulnerable themes. The frequency highlights the importance of proactive maintenance and security practices.
What’s the difference between malware, phishing, and brute-force attacks?
Malware refers to malicious software injected into your site, often used to steal data, redirect traffic, or display spam.
Phishing involves tricking users or administrators into giving away sensitive information, such as login credentials or payment details.
Brute-force attacks use automated bots to repeatedly guess login credentials until they succeed.
Each method has different goals, but all can compromise your website and damage user trust.
Can small business sites be targeted too?
Yes. In fact, small businesses are often easier targets because they typically have weaker security measures than large enterprises. Hackers use automated tools that scan the internet for vulnerabilities, meaning any site—large or small—can be attacked if left unprotected.
What happens if my site is blacklisted by Google?
When Google detects malware or suspicious activity on your site, it may blacklist it to protect users. Visitors will see warnings such as “This site may harm your computer,” and your organic search traffic can drop to near zero. To recover, you must remove the malicious code, secure your site, and then request a review through Google Search Console.
Should I hire an expert or fix it myself?
It depends on the severity of the hack and your technical expertise.If the breach is minor and you’re comfortable following cleanup guides, you may be able to fix it yourself.
For complex attacks, or if sensitive data is involved, hiring a professional security expert is the safer option. They can identify hidden backdoors, clean your files, and implement stronger defenses.
Final Thoughts
Detecting a compromised WordPress site early is critical to minimizing damage. The sooner you recognize unusual behavior, whether it’s strange traffic patterns, unauthorized content, or login issues, the faster you can contain the breach and restore normal operations.
It is important to remember that security is not a one-time setup. WordPress protection requires ongoing attention: updating software, monitoring activity, and responding quickly to new threats. Neglecting even small details can open the door to serious vulnerabilities.
The most effective defense is a layered approach. Combining strong passwords, two-factor authentication, reliable backups, secure hosting, and proactive monitoring creates multiple barriers that make your site far harder to compromise. By treating security as a continuous process rather than a one-off task, you protect not only your website but also your reputation, your customers, and your business growth. For personalized guidance and complete WordPress solutions, connect with the WordPress experts at Jpadweb.